TryHackMe - Reversing Elf - Walkthrough
Introduction
Today we're going to be doing a walkthrough for the Reversing ELF room hosted at https://tryhackme.com/room/reverselfiles . For this walkthrough, we'll be using one virtual machine (VMs), a Kali Linux VM as our attacking machine.
Task 1 - Crackme1
Questions
What is the flag?
Download the Task 1 Task File
Copy it to your working directory
Give the file executable permissions
Run the file
chmod +x crackme1
./crackme1
Task 2 - Crackme2
Questions
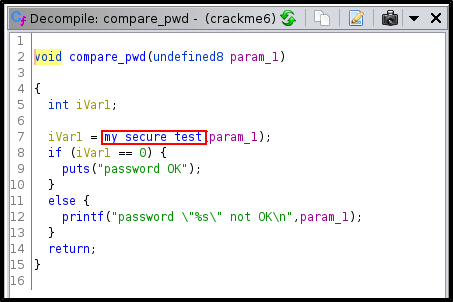
What is the super secret password ?
Give the file executable permissions
Run Ltrace on the file with a test string
chmod +x crackme2
ltrace ./crackme2 test
Task 3 - Crackme3
Questions
What is the flag?
Give the file executable permissions
Run strings on the file
Echo the base64 string you found, pipe it into Base64 decode
chmod +x crackme3
strings crackme3
echo “base64stringFoundInPreviousStep” | base64 -d
Task 4 - Crackme4
Questions
What is the password ?
Give the file executable permissions
Run Ltrace on the file with a test string
chmod +x crackme4
ltrace ./crackme4 test
Task 5 - Crackme5
Questions
Give the file executable permissions
Run Ltrace on the file with a test string
Run the file with the discovered strncmp string as input
chmod+x crackme5
ltrace ./crackme5
input test
./crackme5
input string found in previous step
Task 7- Crackme7
Questions
What is the flag ?
We import the crackme7 file into Ghidra like we did the previous file
In the Symbol Tree window, we select the main function
In the Decompiler window, we see that there's a special response if we enter hex value 0x7a69, which in decimal is 31337:
Task 8 - Crackme8
We import the crackme8 file into Ghidra like we did the previous file
In the Symbol Tree window, we select the main function
In the Decompile window, we see that the function is looking for the value of -0x35010ff3, which in decimal is -889262067.































ReplyDeleteHi dear,
Thank you for this wonderful post. It is very informative and useful. I would like to share something here too. NeTechy.com is Internet Based Blog And Informative Website. NeTechy provides technology and digital marketing blogs and articles. Our goal is to help individuals and businesses in to tech industry with knowledge to be more efficient and tech savvy.
What Are The Best Traffic Sources For Affiliate Marketing In 2021?
Oh wow, I spent hours on task5 cause I fell down a rabbit hole using Ghidra and had a fake flag that was in a common format (eg. text{1337_t3xt_h3r3}). I didn't know about ltrace... can't believe it just gives you the solution :D Thanks very much for this write up, I learned a lot.
ReplyDelete